Over 178,000 SonicWall Firewalls at Risk: Critical Vulnerabilities Expose Devices to DoS and Remote Code Execution
Plus, Phemedrone Stealer Exploits Patched Windows Flaw: Threat Actors Target Browsers, Crypto Wallets, and Messaging Apps
SonicOS Flaws Put Massive Number of Devices in Jeopardy; Critical Patches Urged
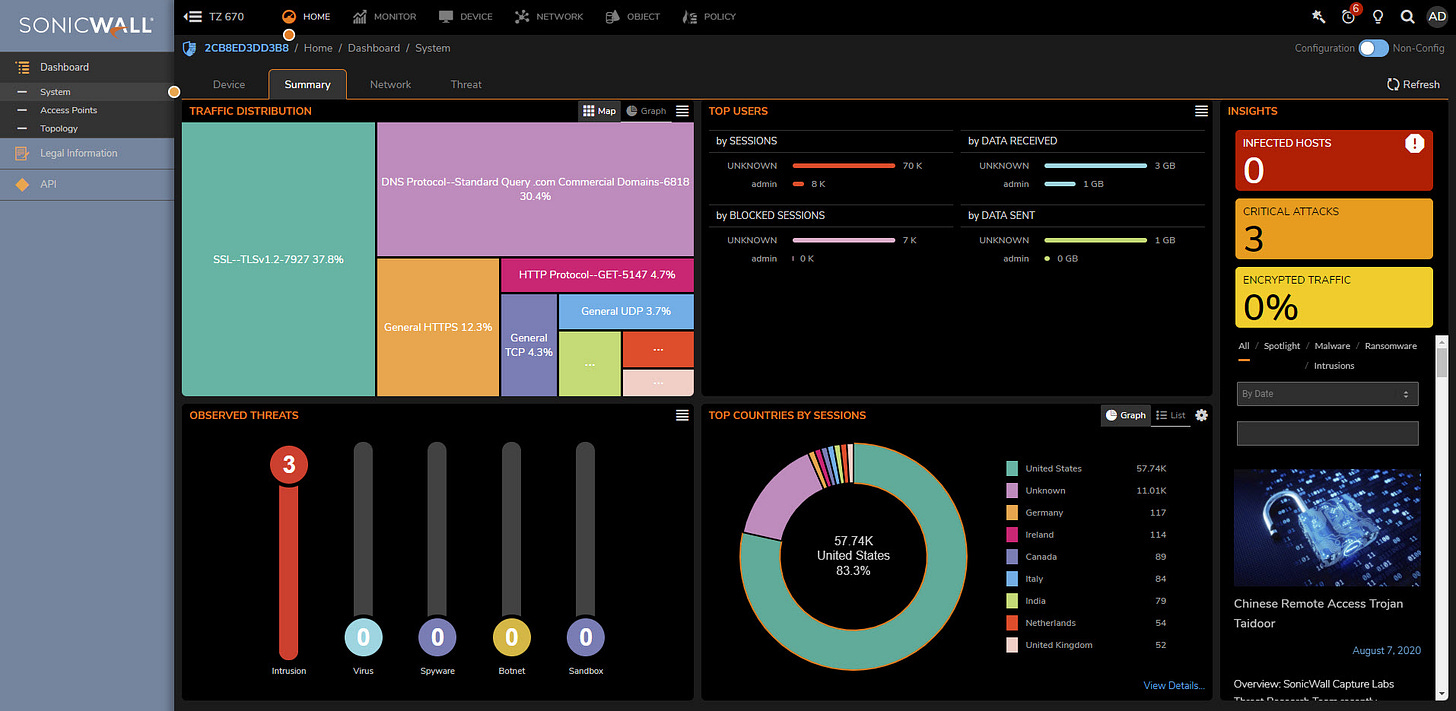
A startling revelation by cybersecurity experts highlights the vulnerability of over 178,000 SonicWall firewalls to critical flaws that could lead to denial-of-service (DoS) and remote code execution (RCE) attacks. The two security vulnerabilities, CVE-2022-22274 and CVE-2023-0656, potentially allow remote, unauthenticated attackers to exploit SonicOS via HTTP requests, triggering stack-based buffer overflows.
Jon Williams, a senior security engineer at Bishop Fox, emphasizes that the flaws, though fundamentally similar, are exploitable at different HTTP URI paths due to the reuse of a vulnerable code pattern. While there are no reports of active exploitation in the wild, a proof-of-concept (PoC) for CVE-2023-0656 was published in April 2023 by the SSD Secure Disclosure team.
The cybersecurity firm emphasizes the potential weaponization of these vulnerabilities by malicious actors to induce repeated crashes, forcing the SonicWall appliance into maintenance mode. This action necessitates administrative intervention to restore normal functionality, posing a significant risk to affected devices.
It's noteworthy that over 146,000 publicly-accessible devices are susceptible to a flaw that was disclosed almost two years ago, underlining the urgency for users to update to the latest versions and ensure that the management interface is not exposed to the internet. The revelation underscores the critical need for proactive measures to safeguard network infrastructure against potential threats exploiting these SonicOS vulnerabilities.
Security Alert: Cybercriminals Utilize Microsoft Windows Vulnerability to Deploy Phemedrone Stealer
Threat actors are capitalizing on a recently patched security flaw in Microsoft Windows to deploy an open-source information stealer known as Phemedrone Stealer, targeting web browsers, cryptocurrency wallets, and messaging apps such as Telegram, Steam, and Discord. Trend Micro researchers identified the active exploitation of CVE-2023-36025, a security bypass vulnerability in Windows SmartScreen, which Microsoft addressed in its November 2023 Patch Tuesday updates.
Phemedrone Stealer's capabilities include capturing screenshots, collecting data on hardware, location, and operating system details, and stealing sensitive information. The stolen data is then sent to the attackers via Telegram or their command-and-control (C&C) server. The attack vector involves the use of malicious Internet Shortcut (.URL) files hosted on Discord or cloud services, exploiting CVE-2023-36025 to execute a control panel (.CPL) file that circumvents Windows Defender SmartScreen.
The researchers outline the infection process, wherein the malicious .CPL file executes a PowerShell loader ("DATA3.txt") that serves as a launchpad for Donut, an open-source shellcode loader. Donut decrypts and executes Phemedrone Stealer, which is actively maintained on GitHub and Telegram by its developers.
Despite the security patch, threat actors persist in exploiting CVE-2023-36025, showcasing their adaptability in evading Windows Defender SmartScreen protections. The incident underscores the ongoing challenges in securing systems against evolving cyber threats, with attackers swiftly incorporating newly disclosed exploits into their attack chains to maximize impact.
Jobs/Internships:
The Trade Desk - 2024 Summer Internship - Software Engineering - Hong Kong
Workato - Intern - Technical Program Manager (Partner Success) - Bangalore, India
Bybit - APP/Mobile Engineer (Full-Time Internship) - Hong Kong, Hong Kong SAR
Spark Investment Management - PhD Computer Scientist/Software Developer $750K++ - New York, NY
Roblox - Principal Technical Program Manager, Engine - San Mateo, CA, United States